 VPN's are not only a good way to surf the internet anonymously and bypass censorship they are getting crucial day by day for users in countries where bittorrent is being targeted, We have been provided with ten 3 months PPTP VPN on Netherland server from CactusVPN for our users, read instructions at the end of this post to get one.
VPN's are not only a good way to surf the internet anonymously and bypass censorship they are getting crucial day by day for users in countries where bittorrent is being targeted, We have been provided with ten 3 months PPTP VPN on Netherland server from CactusVPN for our users, read instructions at the end of this post to get one.
If you are new to the world of VPN's here is a quick starter - A virtual private network (VPN) is a concealed system that interlinks isolated networks throughout chiefly civic statement infrastructures for instance the Internet. VPNs offer great safety via tunneling protocols and safety measures. VPN can moreover be used to inter-relate two same networks above an unrelated center network.
Two major kinds of VPN service present: Remote-access VPNs along with Site-to-site VPNs. First one allows person to hook up to a distant network like itinerant salespeople linking to their company's intranet. VPNs thus shrink expenses as they eradicate the want for committed leased outline amid networks, but as a substitute employ presented infrastructures to bond networks though totaling a sheet of refuge.
There are numerous systems that facilitate you to produce networks by means of the Internet as the standard for transporting facts. These systems apply encryption and added safety mechanisms to guarantee that just certified users can admission the system and that the records are not intercepted.
1. The Point-to-Point Tunneling Protocol (PPTP), formed by Microsoft in concurrence through further expertise companies, is the mainly broadly supported VPN technique amongst Windows customers. PPTP is an annex of the Internet set Point-to-Point protocol (PPP), the association stratum protocol worn to broadcast IP packets above sequential associations. PPTP utilizes similar kinds of confirmation as PPP.
2. The Layer 2 Tunneling Protocol (L2TP) was formed in collaboration involving Cisco and Microsoft to unite features of PPTP with Cisco’s proprietary (L2F). L2TP does not give any encryption or privacy itself. It is based on an encryption protocol that it passes inside the channel to supply seclusion.
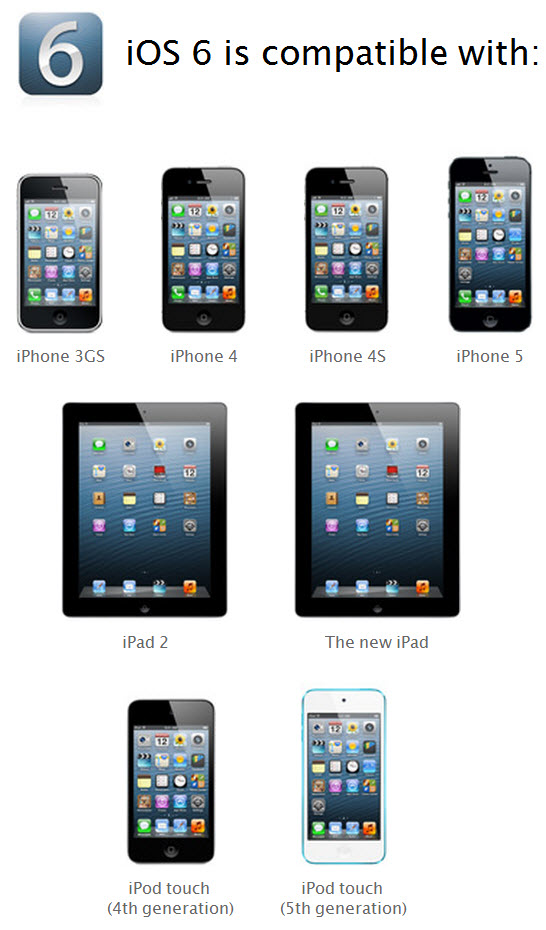
 As announced with Apple iPhone 5, the Apple iOS 6 upgrade made it to public downloading today. According to Apple, iOS 6 has more than 200+ new features and is aimed to deliver a stable and responsive mobile operating-system to all recent iDevice.
As announced with Apple iPhone 5, the Apple iOS 6 upgrade made it to public downloading today. According to Apple, iOS 6 has more than 200+ new features and is aimed to deliver a stable and responsive mobile operating-system to all recent iDevice.

 After
After 
 After successful
After successful 
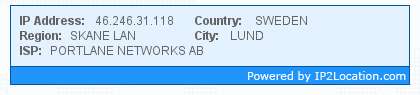

 VPN's are not only a good way to surf the internet anonymously and bypass censorship they are getting crucial day by day for users in countries where bittorrent is being targeted, We have been provided with ten 3 months PPTP VPN on Netherland server from CactusVPN for our users, read instructions at the end of this post to get one.
VPN's are not only a good way to surf the internet anonymously and bypass censorship they are getting crucial day by day for users in countries where bittorrent is being targeted, We have been provided with ten 3 months PPTP VPN on Netherland server from CactusVPN for our users, read instructions at the end of this post to get one.