We have already seen how vulnerable routers can be a security threat, but ASUSTeK Computer Inc (ASUS) made everything feel small by leaving two critical flaws allowing anybody in the world to simply open a web-browser and access any Asus routers data with full read-write permission by simply typing a URL. This is not all, when notified about the severe design flaw, the company did nothing and ignored emails and phonecalls by researcher Kyle Lovetts who discovered the flaw.
To make their point and expose the vulnerability, a group did some guerrilla styled attack hacking into 13,000+ IP addresses using vulnerable Asus routers and left a text-file explaining the hack into user's router attached media disks. The text file informed users : "This is an automated message being sent out to everyone effected [sic]," the message, uploaded to his device without any login credentials, read. "Your Asus router (and your documents) can be accessed by anyone in the world with an Internet connection. You need to protect yourself and learn more by reading the following news article: http//nullfluid.com/asusgate.txt."
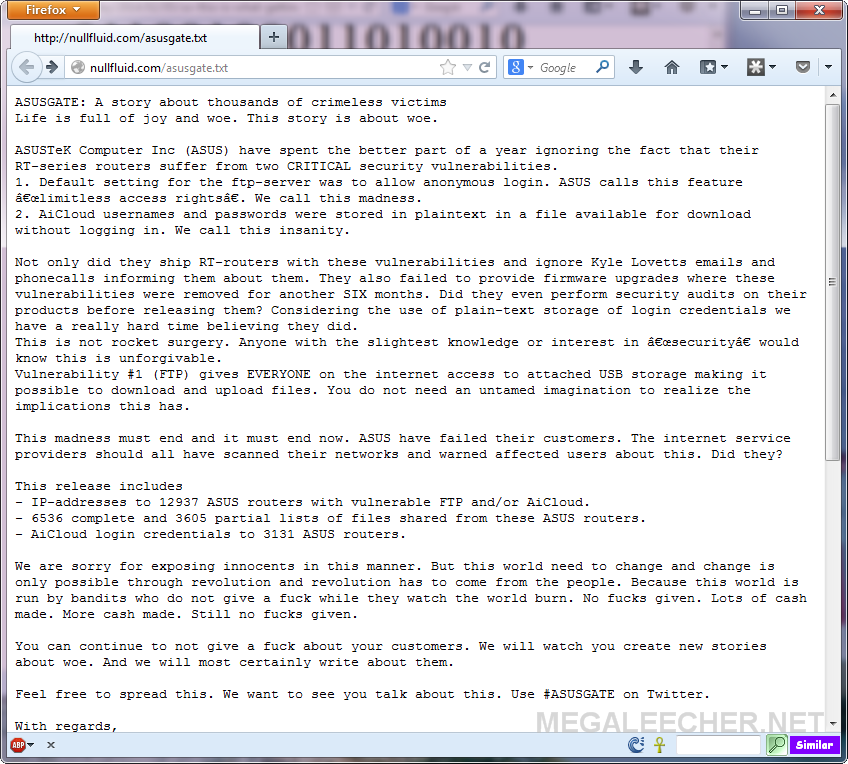
Visiting the mentioned url (as shown below), shows details about the exploit and how Asus has left users with an wide-open ftp server allowing anonymous login with full read-write privilege and AiCloud usernames and passwords stored in a plaintext file which is available for download without logging in. The group also made public a torrent link containing 10,000+ list of files stored on the Asus-connected hard drives for anybody to access.
 Photos are one the most important memories of your life which nobody would like to loose, luckily there are chances of data recovery even after an accidental deletion and professional utilities like "Wondershare Photo Recovery" comes to a user's rescue in such bad situations.
Photos are one the most important memories of your life which nobody would like to loose, luckily there are chances of data recovery even after an accidental deletion and professional utilities like "Wondershare Photo Recovery" comes to a user's rescue in such bad situations.