Submitted by Deepesh Agarwal on Tue, 01/20/2009 - 10:34
High risk Microsoft Windows worm Win32/Conficker is on the rise, according to a report by F-Secure a fresh variant of the worm is propagating fast and has already infected more then nine million computers exploiting Windows Server service vulnerability, once infected the user is being prevented from visiting anti-virus and anti-malware websites making it very difficult to fix the infection.
How Win32/Conficker Spreads
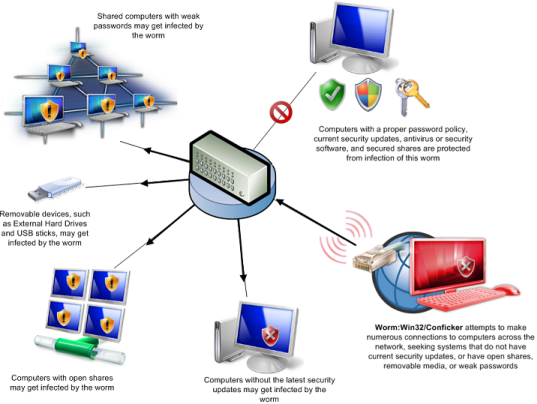
Microsoft has issued a fix long back in last October via Security Update MS08-067, if you are not infected you can apply the patch and get secured against the vulnerability, however, if you are already infected download the free Removal patch from F-Secure from the link at end of the post.
Microsoft Patch KB958644
Download:
- Microsoft Security Update MS08-067 (Patch for fixing the security hole)
- F-Secure removal tool (use this if already infected).
Comments
Conficker.B High Risk !!
This is a hell smart worm :
Conficker.B uses the Conficker.A approach, plus a whole lot more — as a "blended threat," it's an equal-opportunity infecter. The MMPC's TechNet blog offers an excellent, graphical overview of the ways that Conficker.B can get into your network. Here are the main attack vectors:
Conficker.B uses the old Conficker.A approach: simple Trojans that arrive via e-mail or by downloading an infected program.
Once a PC on a network is infected, Conficker.B reaches across the network to see whether any of its PCs have not yet patched the MS08-067 hole. After infecting these unprotected PCs, Conficker plugs the MS08-067 hole, presumably so other, similar worms can't get in. What a sneaky buzzard!
If Conficker.B finds that it can't get into a computer via the MS08-067 hole, it tries to break in by using the standard Windows admin account, entering each of 248 common passwords. This weak password list (which you'll find under the Analysis tab) includes such all-time favorites as admin, mypass, test, foo, 1111, and many others you may have seen before.
Once Conficker.B gains entry to a networked machine, it drops a copy of itself onto the target's hard drive and creates a scheduled job that runs the infected file. Conficker.B also loads itself onto all accessible shared folders. Ho-hum.
Finally, Conficker.B scans and infects all removable devices on the system, including USB drives and external hard drives.
YTWY
WETERTYTEY
Add new comment